Malware analysis Suspicious activity
4.9
$ 28.50
In stock
(297)
Product Description

How to Detect New Threats via Suspicious Activities
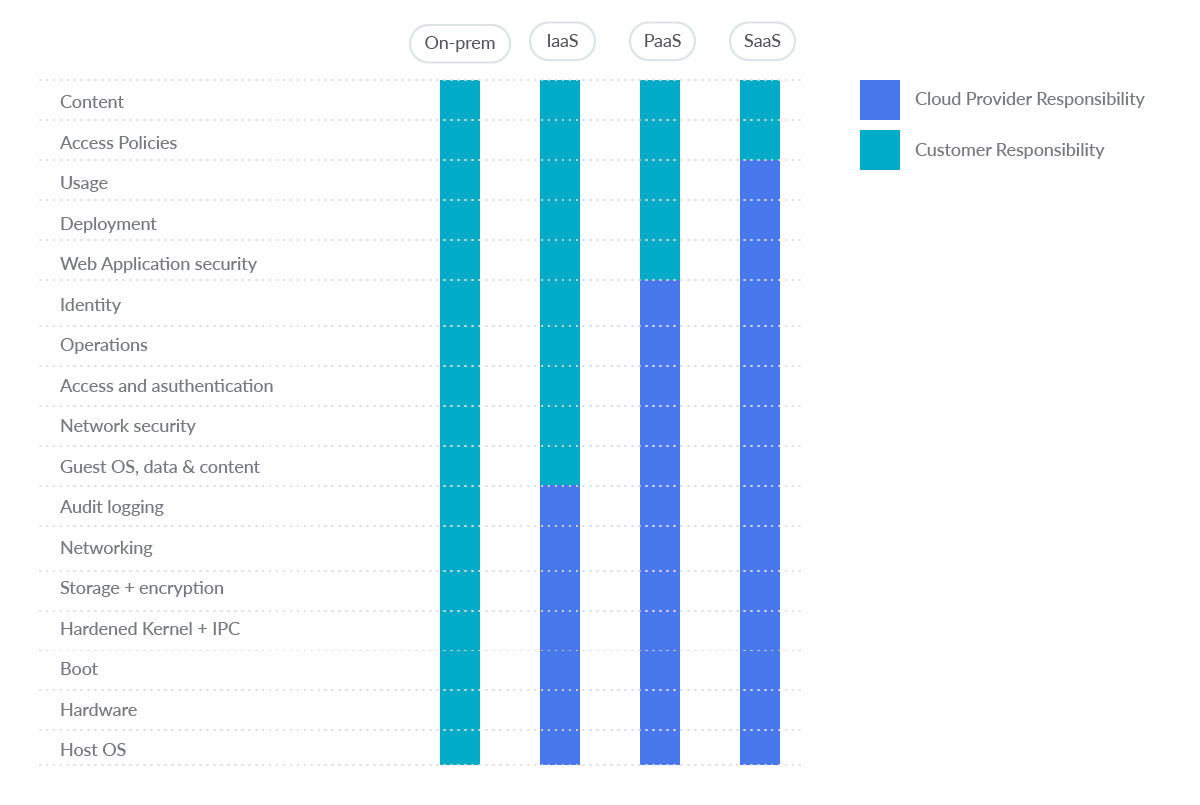
Detecting suspicious activity on AWS using cloud logs - Malware
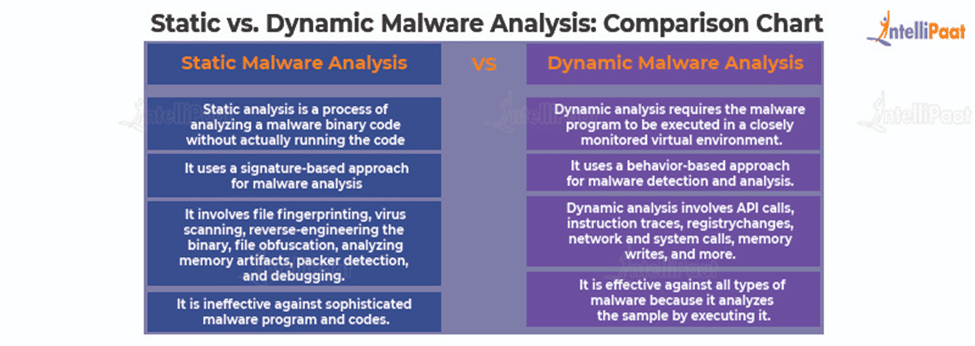
What is Malware Analysis?: Types and Stages Explained

How to Detect New Threats via Suspicious Activities

Malware Analysis: Steps & Examples - CrowdStrike
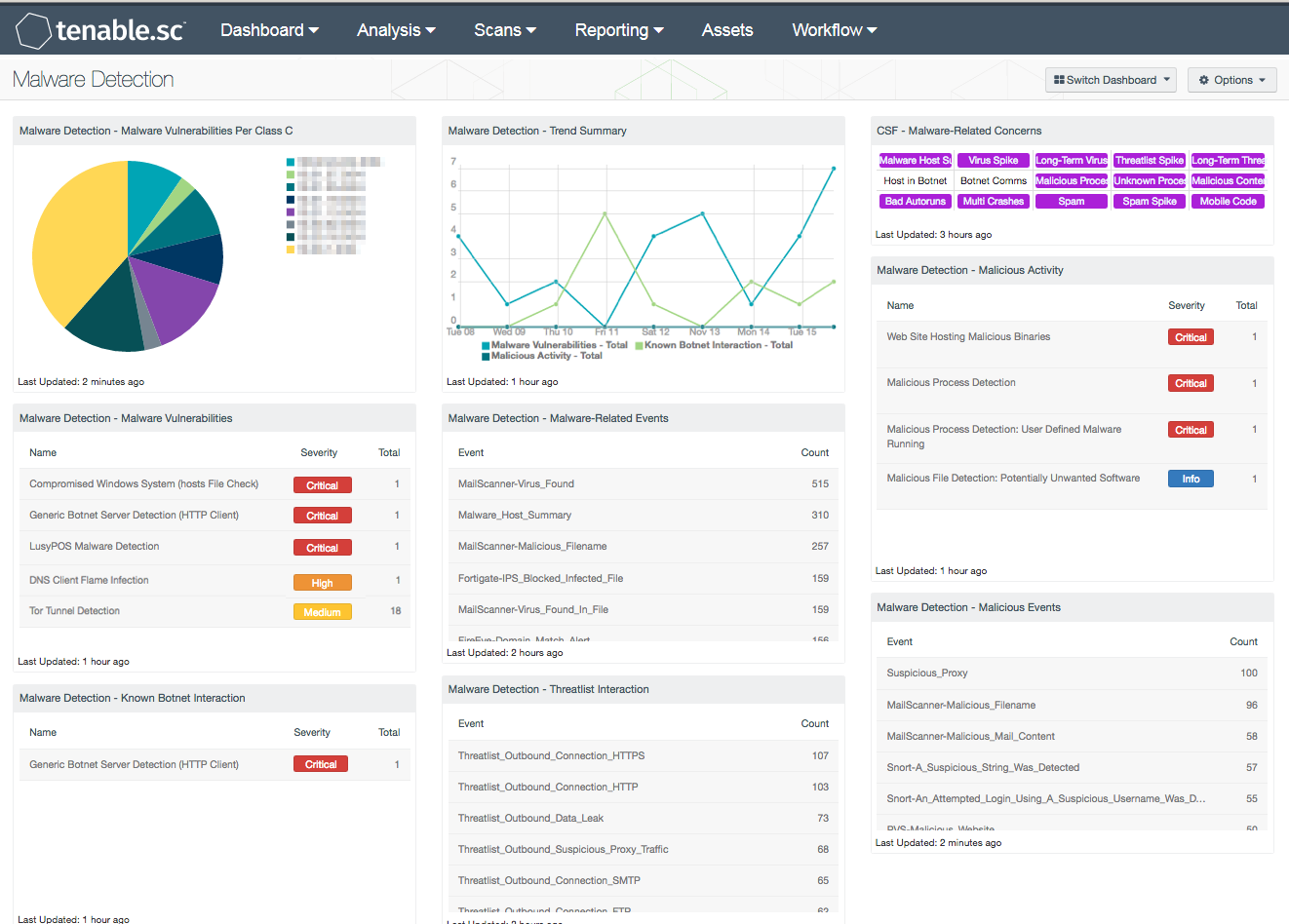
Malware Detection - SC Dashboard

Top 10 Malware Analysis Platforms & Tools

Tools and Techniques for Collection and Analysis of Internet-of

Malware Analysis: Tips & Tricks Poster

Malware Analysis Benefits Incident Response

Behavior-based malware analysis process as conducted by our

Operation Triangulation: iOS devices targeted with previously
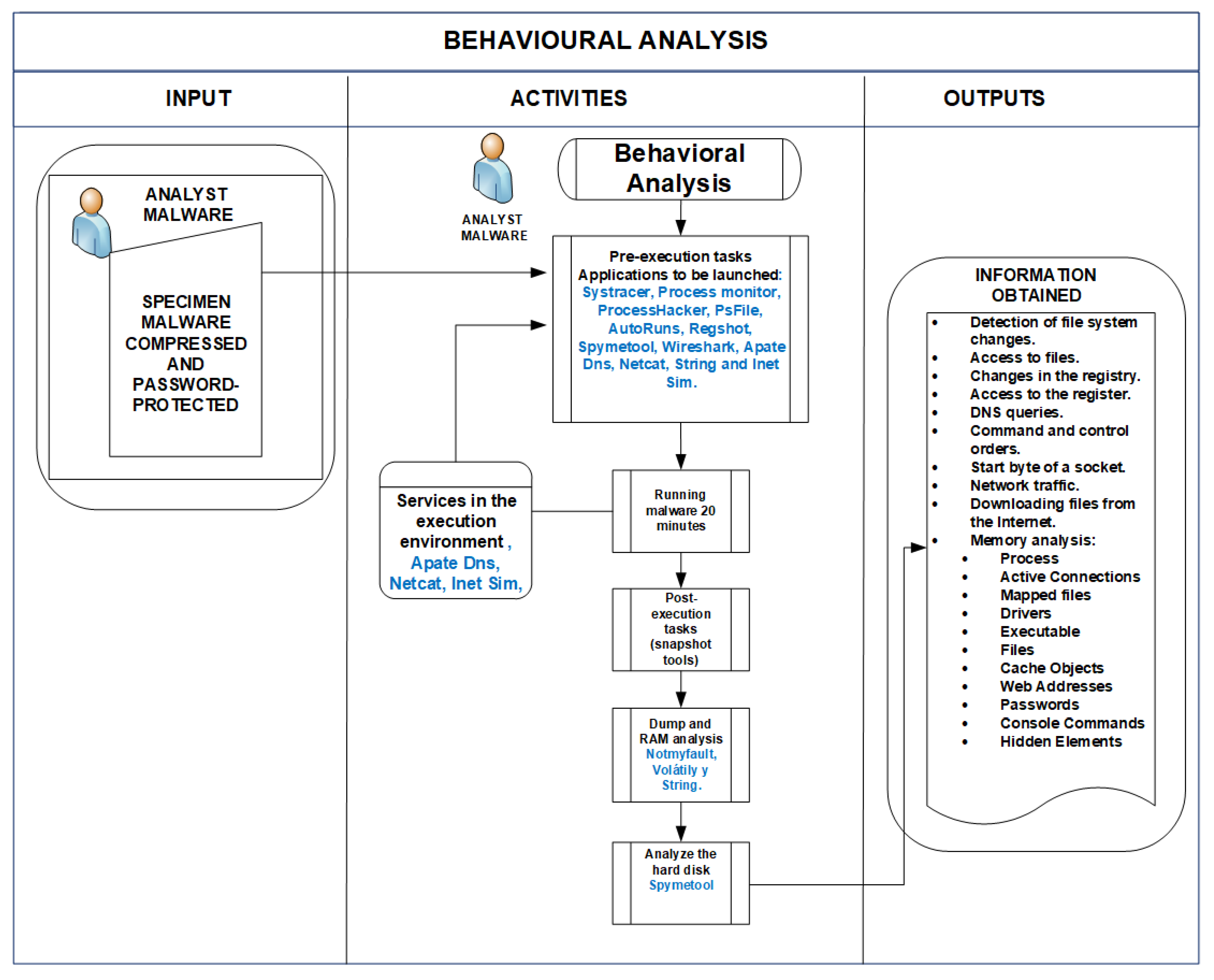
Applied Sciences, Free Full-Text